One of the major appeals of Cyberpunk 2077′s, er, cyberpunk setting is the ability to hack just about anything electronic. Hacking stuff was a big part of the original tabletop Cyberpunk module, and that’s carried over into this game. Here’s how to use Breach Protocol in Cyberpunk 2077.
How to Breach Protocol in Cyberpunk 2077
In Cyberpunk 2077, attempting to Breach Protocol will enter you into a short minigame where you will have to a code sequence. There are multiple circumstances where you would need to Breach Protocol. You can use it on enemies or networked equipment to apply RAM buffs to your quickhacks. You can breach terminals around the map to extract eddies and quick hack components. Some parts of various jobs and gigs will also have you going the breach hack, such as decrypting shards.
Perks and Cyberware
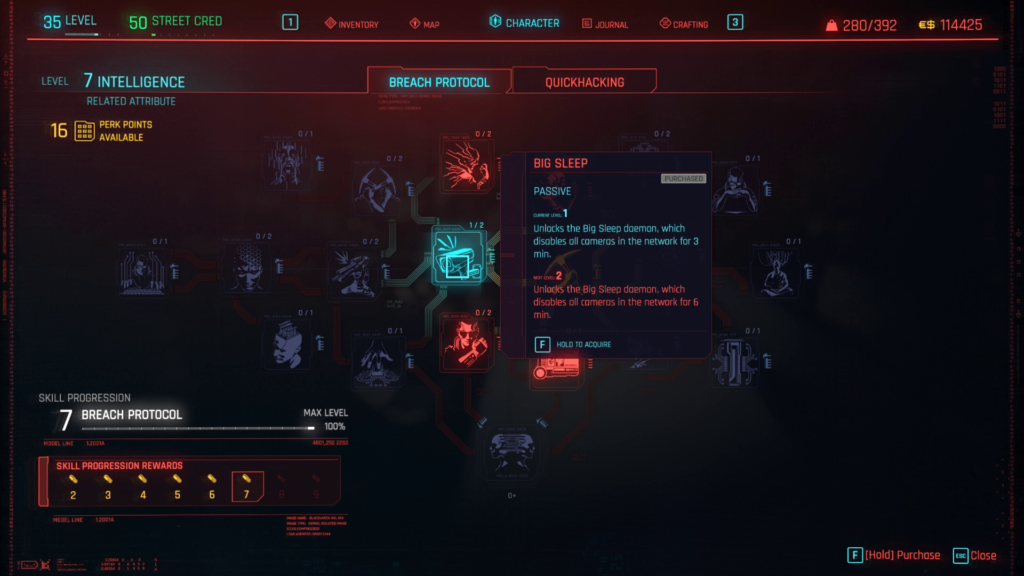
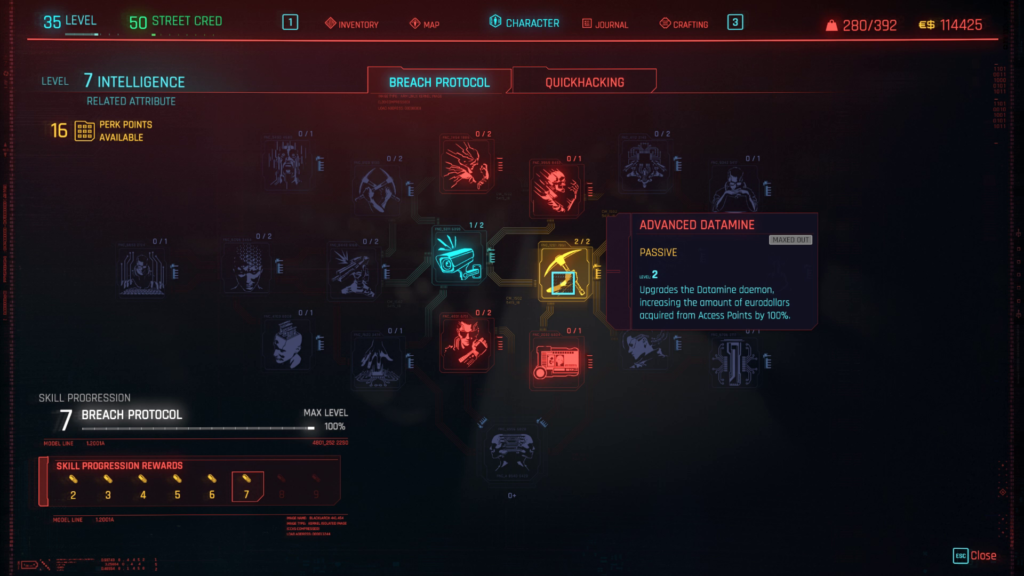
First, let’s review some of the perks and cyberware we will want to make our breaching easier and more powerful. The perks are optional but very helpful. The two perks we recommend are Big Sleep and Advanced Datamine. Both of these perks can be found under the Breach Protocol tree inside the Intelligence attribute.
The Big Sleep perk will allow you to disable all the cameras in a network when you attempt to do a protocol breach. This is super useful since it will save you RAM on your quickhacks when you go to disable cameras. The Advanced Datamine perk increases the amount of eddies you get when you breach an access terminal, giving you a nice boost in cash flow.
For your cyberware, you will want to upgrade your Cyberdeck as soon as you can. An upgraded cyberdeck will increase your Buffer Size when you are performing a breach. This will allow you to enter more sequence numbers and give you a more considerable margin of error.
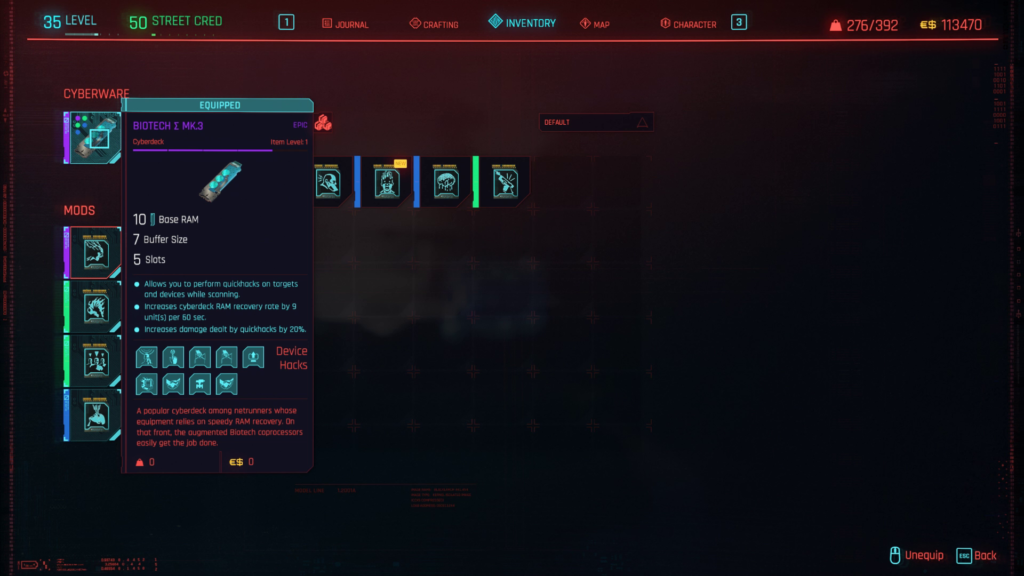
Breach Protocol Screen
The Breach protocol screen has four sections to it.
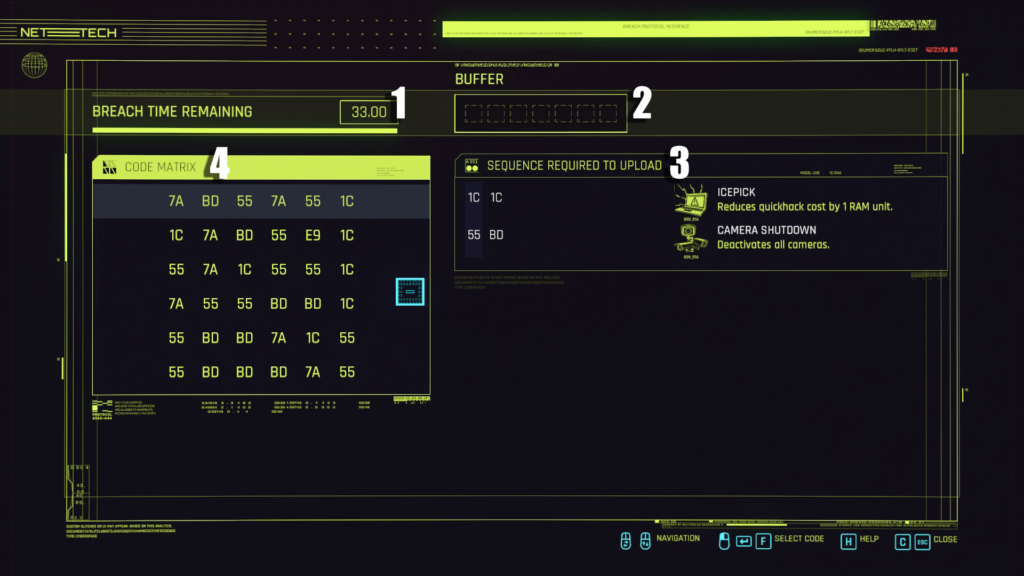
- Breach Time Remaining is the countdown timer. This timer will start counting down as soon as you choose your first number. For this reason, it doesn’t make much sent to get perks that increase this timer since you can plan your sequence before starting it.
- Buffer is your entered sequence. The size of this buffer and how many numbers you can enter into it is determined by your Cyberdeck.
- Sequence Required to Upload is the sequence you are trying to hack or match. The different rows here will represent different levels of the hack. You can pick one or all of the sequences to go for.
- Code Matrix shows the numbers you can choose from for the sequence. Clicking these will put them into the buffer.
How to Breach Protocol
You will breach a protocol by picking numbers from the code matrix to match them to the Sequence Required on the right. The Code Matrix will apply some restrictions on you. When you start you will only be able to pick a number from the first row. After you pick the first number, you will only be able to pick from the column of that number. Then again back to the row for the first choice.
You will always pick from left to right, then up and down, then left to right continuously until you have completed the sequence. If you hover over your number choice, you will see it will highlight the next column or row so you can plan better. If you hover over the number on the right sequence panel, it will show you all occurrences of that number in the code matrix. This can help you plan as well before you start the breach timer.
An Example
Let’s take a look at an example.
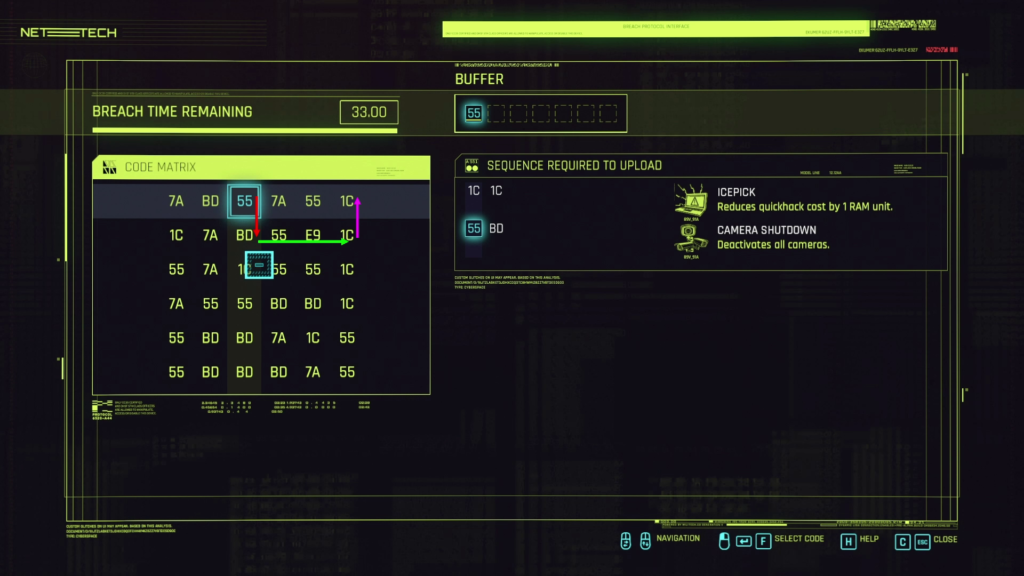
You can see here that we have two sequences we can finish.
1C 1C
55 BD
We have to start in the first row, and our options are
7A BD 55 7A 55 1C
We can start with either of the two 55’s or 1C. Looking at the first 55 we will be able to choose BD as our next option and complete the Camera Shutdown sequence. This will also allow use to pick 1C in the row and then 1C again in the column completing the Icepick sequence.
7A BD 55 7A 55 1C
BD 55 E9 1C
1C
55
BD
BD
So our first choice was left/right for 55, then up/down for BD then left/right for 1C and up/down for the last 1C.
All breach sequences will follow this pattern. You won’t always be able to complete all of the sequences, but there is always a solution for at least one. If you are doing a datamine extraction, always go for Datamine V3 as it will give you the most rewards.
Now you know How to Breach Protocol in Cyberpunk 2077. We hope you found this guide helpful and this breaching minigame is a little bit easier for you.



Published: Dec 23, 2020 07:18 pm